New computer virus causes havoc
A powerful new computer virus was today causing havoc with e-mail systems across the world.
Experts described the virus, called Goner, as one of the fastest-spreading they had yet seen and warned computer users to immediately delete it if they received it.
Alex Shipp, spokesman for anti-virus service MessageLabs, said: “It’s spreading with tremendous speed and thousands of users in Britain have already been sent it.
“The virus mass mails itself out through e-mail and attempts to destroy anti-virus software on computers, which could prove extremely problematic for those unfortunate enough to receive it.”
The infected e-mail has the word “Hi” as its subject and body text which reads “When I saw this screen saver, I immediately thought about you. I am in a harry (sic), I promise you will love it.” Its attachment is labelled “gone.scr.”
It was first detected this morning in the US but experts believe it was created in Europe.
The US, the UK and France are the worst hit of the 17 countries affected so far.
Mr Shipp said: “We had a handful of reports this morning but at mid-afternoon in the UK it went mad. We have had about 30,000 reports and the figure is rising.”
A criminal investigation has now been launched in an effort to track down the person responsible for the virus.
Previous viruses, such as Love Bug, Code Red and the Nimda Worm caused problems for millions of computer users across the world.Share or comment on this article: {“status”:”error”,”code”:”499″,”payload”:”Asset id not found: readcomments comments with assetId=88046, assetTypeId=1″}
02
How Do Computer Viruses Actually Work?
Welcome back to Ask Giz, the series where we take your questions from all across the tech and science worlds, and attempt to answer them.
We’ve had a little hiatus since our last Ask Giz, but we’re back and Giz-ier than ever. If you’d like to submit a question, feel free to on our official submissions page.
Today’s question comes from Sonia in North Lakes. Sonia wants to know: How do computer viruses actually work?
This is either a really simple question or an excruciatingly complicated one, so we’re going to stick to making it as clear and concise as possible. Let’s dive into it.How do Computer viruses actually work?
Computer viruses, or malware (as in ‘malicious software’), work by infecting computers and injecting a malicious program, similar to how biological viruses infect living beings. Much like biological viruses, the form a computer virus can take varies drastically, depending on the type and what a potential malicious actor is attempting to achieve.
For example, the WannaCry virus that infected computers all around the world in 2017 was a form of ransomware – an attack that, when it infected your computer, would demand a payment to the hacker before unlocking it. The WannaCry virus worked by exposing a technical vulnerability in the code of Windows operating systems, which had been patched in a later update. To compare this to real-world viruses, think about how your immune system may be compromised if you’re not getting all the right nutrients and vitamins to stay healthy. Software updates are like vitamins, or immune system boosters (if we keep the analogy going), but some viruses can still get through.
The trick to the WannaCry virus was that it took advantage of people and businesses that weren’t updating their operating systems, leaving them susceptible to attack.
“Were it not for the continued use of outdated computer systems and poor education around the need to update software, the damage caused by this attack could have been avoided,” antivirus company Kaspersky wrote in a blog post.
Other viruses work by similarly taking advantage of software vulnerabilities, although not every virus is designed to financially compromise the user. As written by High Touch Technologies, other virus types can sabotage your system by being RAM and resource-intensive, can hijack your browser to send you to specific websites, can compromise your saved email addresses, and can overwrite system files to inject malicious alternatives. Some viruses are even designed to compromise your entire local internet network and spread to other computers connected to it.
The term ‘trojan horse’ is often used when defining viruses, but the term is really used to describe a way viruses can be disguised when entering your system – by looking like legitimate software or files.
The best way that you can avoid viruses comes down to three key things:Keep your system updated to the latest version, and regularly update itBe aware of the risks, and use antivirus softwareOnly download files and programs from legitimate or trusted sources, and be aware of websites that may look legitimate, but are not.
On that last point, be aware of websites that appear to look legitimate but are in fact just pretending to be so. The URL ‘YouTube.com’ is the trusted web address of YouTube, Google’s video-sharing website, however, be aware of the spelling: ‘YuoTube.com’ or ‘YouTobe.com’ may in fact direct to untrustworthy websites. By extension, be very careful when you’ve been sent a link from someone you don’t know – it could be to a malicious website.
Take a look at our Complete Guide to Not Getting Hacked for some tips.
If you’d like to submit a question to be answered in a future Ask Giz instalment, we’d love to hear it.
Ask Giz is a fortnightly series where we answer your questions, be it tech, science, gadget, health or gaming related. This is a reader-involved series where we rely on Gizmodo Australia’s audience to submit questions. If you have a question for Giz, you can submit it here. Or check out the answer to our last Ask Giz: Can You Plug Too Many Things Into An Outlet?
03
Xkcd’s Virus Aquarium Made Real
A surprising number of projects here are in some way influenced by the webcomic xkcd, but usually not as directly as this. Comic 350, “Network” is the tale of a very odd stickman who keeps multiple VMs running an unprotected, old version of Windows. Between the VMs, they have virtually every virus and are, effectively, a computer virus aquarium.
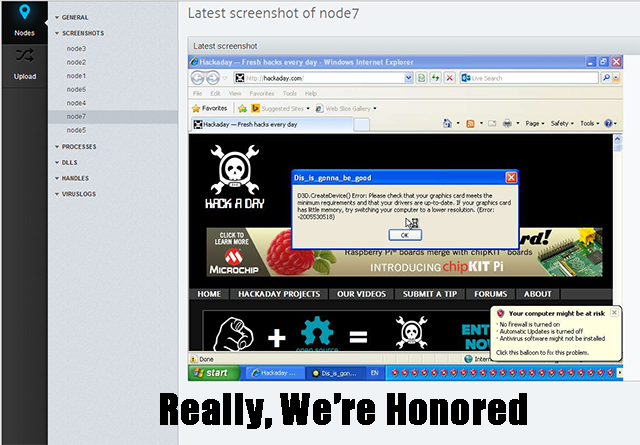
Now it’s a real thing, and best of all, it’s open to the Internet for normal humans to view, complete with screencaps of all seven nodes updated every 30 seconds, the ability to view all processes on each node, and anyone on the Internet can upload any file to a node. All the files uploaded to the nodes are executed, so you get to see in real-time what the effects of “1TB_of_porn_this_took_a_while_to_upload.exe” are on node 3.
The idea of a virus aquarium is cool, but this actually gets much, much more interesting when the project metas itself. Every 24 hours, a virus scanner runs on each node. As of right now, all the nodes are clean making this not a virus aquarium, but a script kiddie aquarium. On at least one node, TeamViewer is running but your guess is as good as mine as to how anyone will get that working.
Edit: Thank you to the person who loaded Hackaday on one of the nodes.
Post Comment